Top Security Pitfalls in the Software Development Life Cycle
The Software Development Life Cycle forms the basis of developing secure applications. Each of the stages has its own security aspects, and any neglect can result in major vulnerabilities. This article identifies typical security lapses in the SDLC and recommends remedies.
- June 2, 2025
- by Tarun


In software development, a structured method of application creation processes is defined in the Software Development Life Cycle (SDLC). Although planning, design, development, testing, and deployment are emphasized in the SDLC, security is often relegated to an afterthought. Neglecting security can lead to an application becoming vulnerable, which can incur costs for development teams to fix and seriously tarnish the reputation of an organization.
Security should flow through each of the SDLC stages, which is known as the Secure Software Development Life Cycle (SSDLC). By recognizing and treating security risks early in development, businesses can greatly minimize the chances of breaches and guarantee the integrity of their applications.
This article looks at important security failure points during the SDLC, covering how these vulnerabilities are introduced and providing practical ways to prevent them. Knowing these risks will also be useful to developers, security practitioners, and organizations trying to achieve the purpose of building secure and resilient software systems.
Lack of Threat Modelling
Understanding the Risk
Threat modelling is a proactive approach to identifying a potential security threat that must take place while designing the system. Without this, attackers may exploit critical vulnerabilities that the development team could miss during the production phase. Threat modelling helps in understanding the attack vectors possible and at the same time knowing how design decisions may impact the security of the system.
Mitigation Strategy
- Early in the design phase, conduct threat modelling sessions that can identify threats and mitigate them in the design.
- Use appropriate frameworks such as STRIDE or PASTA for systematic threat analysis.
- Integrate cross-functional teams, such as security experts, to ensure threat identification.
- Regularly update the threat model as the application keeps evolving to cater for new threats.
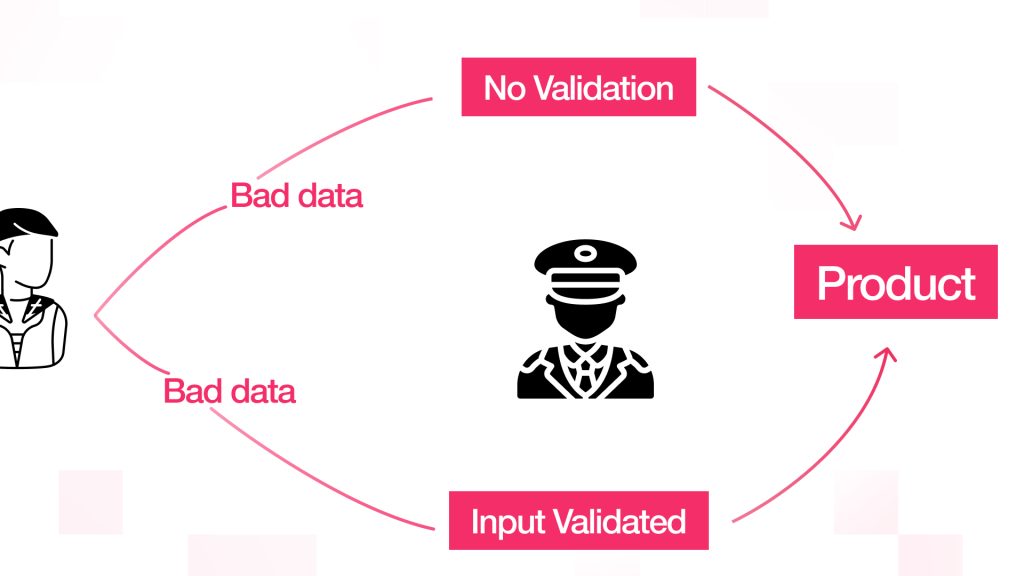
Insufficient Input Validation
Understanding the Risk
Lack of validation for user inputs induces many kinds of vulnerabilities, such as SQL injection and cross-site scripting. These types of attacks tend to corrupt data integrity and application security. Hackers easily manipulate unvalidated inputs and execute malicious code or unauthorized access to data.
Mitigation strategy
- Use a whitelist approach in input validation to ensure that the system processes only expected and safe inputs.
- Secure coding practices and parameterized queries are best for prevention against injection attacks.
- Reassess and update audit checks on validation processes consistently to align with emerging threats.
- Train developers in secure coding to prevent them from introducing vulnerabilities.
Need a Secure Development partner to help grow your Business?
Our Experts Can Help!
Insecure Dependencies
Understanding the Risks
Most modern applications rely on various of third-party APIs, libraries and frameworks. Use of old or vulnerable sources exposes applications to numerous security risks, with attackers taking advantage of known flaws in these components to compromise application integrity.
Mitigation Strategy
- Update and patch dependencies regularly and use tools to keep track of known vulnerabilities in the third-party component.
- Keep an updated record of all the components used by applications, along with their versions.
- Set up a process that appraises and approves new dependencies before adding them to the application to ensure that these dependencies meet compliance standards.
- Lastly, educate development teams on the aspects of risky usage of insecure dependencies and the importance of doing regular updates.
Inadequate Authentication Method
Understanding the Risks
Poor authentication mechanisms, such as hardcoded credentials or no multi-factor authentication (MFA), can enable unauthorized access. Attackers can exploit these vulnerabilities to some sensitive data and systems.
Mitigation Strategy
- Implement strong authentication mechanisms, including MFA and secure password storage methods.
- Implement secure protocols for authentication, with periodic audits of the authentication procedures.
- Create user awareness of the importance of strong passwords and secure authentication methods.
- Security teams should closely monitor any atypical behaviour or actions observed in authentication logs, as these could indicate attempted breaches.
Are you an ecommerce business worried about data security? Here are some tips to secure data and prevent cybercrime.
Poor Session Management
Understanding the Risks
Improper session management can create the dangerous threats of session hijacking and unauthorized access to user accounts. Weaker session management has become reliable grounds for impersonating users to access their sensitive information.
Mitigation Strategy
- Secure and effective session management techniques: appropriate session timeouts, secure cookies, session validation mechanisms, and anomaly detection with monitoring session activities.
- Users should be sensitized on the importance of logging out from shared or public devices.
- Frequent reconnaissance supervision and updating of session management practices to power current threats will be a benefit.
Security Misconfiguration
Understanding the Risks
Application attacks may result from default configurations or faulty settings. Attackers can exploit leaving unnecessary services enabled or using generic passwords from these two examples. Misconfiguration can also lead to other vulnerabilities that unauthorized persons can misuse to gain access.
Mitigation Strategy
- Establish a regular process to review and update configurations, such as disabling unnecessary services or changing default credentials.
- Use tools to automate misconfiguration detection and enforce security policies.”
- A process should be created for secure management and maintenance of configuration files.
- Educate all administrators on the risks surrounding misconfigurations and the importance of secure settings.
Insufficient Logging and Monitoring
Understanding the Risks
Security incidents become more difficult to spot and respond to within a system without proper logging and monitoring. Visibility into application activities is not permissive for incident detection and response allowing attackers more scope for operation.
Mitigation strategy
- Implement comprehensive logging and monitoring for early detection of unusual activities and possible security breaches.
- Protect the logs against tampering and conduct regular reviews for suspicious activity.
- Build a centralized logging system to enable efficient analysis and correlation of events.
- Train the teams on the importance of detection and response timing in security incidents.
Looking for a Partner in Your Secure Software Development Journey?
We Can Help!
Failure to Encrypt Sensitive Data
Understanding the Risks
Storing or transmitting sensitive data without encryption can lead to data breaches and loss of confidentiality. Attackers can intercept unencrypted data to gain access to sensitive information.
Mitigation Strategy
- Use strong encryption methods for data at rest and in transit to protect sensitive information.
- Implement key management practices and ensure compliance with data protection regulations.
- Regularly audit encryption mechanisms to ensure their effectiveness. Ensure that all encryption libraries used are up to date and come from trusted sources.
- Sensitive data should never be stored or transmitted in plaintext, including passwords, personal information, financial details, or business-critical records. Avoid creating custom encryption algorithms—use proven, industry-standard solutions like AES-256 for data at rest and TLS 1.3 for data in transit.
- Implement secure key rotation policies, store cryptographic keys separately from the data they protect, and limit access to those keys using strict access controls.
- In cloud environments, use platform-native encryption options and configure them according to best practices recommended by cloud providers.
Lack of Security Testing
Understanding the Risks
Most organizations spend a lot of effort on functional testing that the software meets end user expectations, forgetting about vulnerability testing. Security testing is an important part of discovering potential threats, insecure coding patterns, or misuse of third-party assets before going live. Without it, they are typically discovered after deployment and often by outside malicious actors. Security flaws in production could lead to data breaches, compliance violations, and loss of customer trust.
Mitigation Strategy
- Integrate security testing into the Software Development Life Cycle process, not just at the end. Instead, include Static Application Security Testing (SAST) to catch issues that arise during coding and Dynamic Application Security Testing (DAST) during runtime.
- Conduct regular manual code reviews with a focus on security and encourage the use of tools like linters and secure code scanning as part of CI/CD pipelines.
- Simulate real-world attacks through penetration tests and bug bounty programs.
- Security testing needs to be a continuous activity, responding to changes in code, infrastructure, and threat landscapes.
Insufficient Security Testing
Understanding the Risks
Even the best tools and frameworks can never safeguard the development team if the team does not understand what secure development really is. One can understand that untrained developers, testers, and project managers are the ones who often write insecure code, misconfigure systems, or fail to identify possible threats. The lack of knowledge about security sows the seeds of some of the recurring vulnerability causes, especially in organizations that seem to rush or do not have a formal security policy in place.
Mitigation Strategy
- Design an exhaustive compulsory security training program for each of the technical team members like developer, QA engineers, DevOps, system architect, and others.
- The training should cover guidelines for secure coding practices; vulnerabilities – both general and those in the OWASP Top Ten; secure software design; and incident response.
- Add a laboratory for hands-on experience to the curriculum. Also, supply supplemental current documentation. Metric performance in security; create a culture where security is everyone’s responsibility; encourage and use security champions or liaisons to further collaboration between security and development teams.
Additional Pitfalls to Avoid
While the previously mentioned top ten are amongst the most common and critical, there are other related security gaps that organizations frequently face in the Software Development Life Cycle:
Weak Access Control
- Risk: If roles and permissions are not defined or enforced appropriately, unauthorized users may access sensitive functions or data.
- Prevention: Role assignments are made using the least privileges and testing of authorization logic as stringently as authentication.
Ignoring Compliance Requirement
- Risk: It would incur major adverse legal and financial repercussions for failing to comply with the reams of regulations from which GDPR, HIPAA, or PCI-DSS are but three.
- Prevention: Involve the legal and compliance teams at the start of the development cycle. Make sure such requirements are included in the design and implementation.
Absence of Incident Response Planning
- Risk: The absence of a plan makes the organizations tend to have a slower, more inefficient response against a breach.
- Prevention: Prepare, continually keep an incident response plan up to date, undertake exercises through tabletop simulations and define the roles in accordance with effective reaction.
Hardcoded Secret and Credential
- Risk: The storage of credentials directly in the source code exposes them whenever the source code is leaked or exposed.
- Prevention: Secrets are to be stored in folder vaults (for example, HashiCorp Vault, AWS Secrets Manager) while credentials are regularly rotated.
Conclusion
Security must be incorporated into the Software Development Life Cycle, and it should not be an afterthought or phase optional. In fact, at every stage of the SDLC — from requirements to maintenance—there are opportunities for strengthening or weakening the security posture of an application. Businesses can fortify their systems, users, and reputation by tackling a few major pitfalls mentioned above, such as immediately creating secure practices at the core development workflow.
The modern threats are so sophisticated that attackers are on constant lookout for any weakness they can exploit. It is the duty of every person in the software development lifecycle to combat these threats, and not just the security teams. Security-aware design, secure coding, periodic testing, and continuous education are the pillars of any solid software security program.
Building secure software is not only about creating a product free from vulnerabilities; it is also about constant, conscious processes that acknowledge and minimize risk. An organization that implements security as an integral milestone in its SDLC will limit the opportunity for exposure, thus ensuring regulatory compliance and delivery of trustworthy software for use by the client.
 Shopify
Shopify

















